If you’ve encrypted a removable USB drive with USBCrypt, you know your files are safe: if you lose the drive, no one will be able to get your files without the correct password that you’ve set up, and the only loss you do suffer in such a case is the cost of the physical drive itself. Still, wouldn’t it be nice to get the drive back anyway?
You can increase the chance of getting your encrypted drive back by putting a message on it to be seen by the person who finds the drive. USBCrypt makes it easy to create such a message: just enter the appropriate text as the host disk name when encrypting the drive:
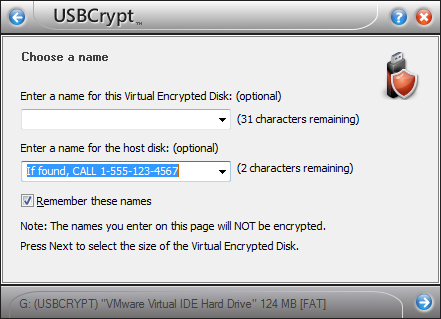
(If you’ve already encrypted the drive, you can change the host disk name with the Rename host disk command). The host disk name is the first thing the person sees after plugging the drive in the computer:
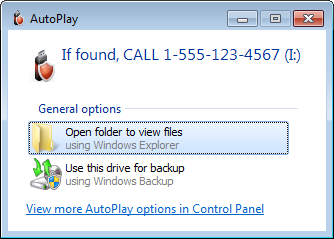
Even if the computer happens to have the autoplay function disabled, the person would see the message when s/he opens the Computer folder:
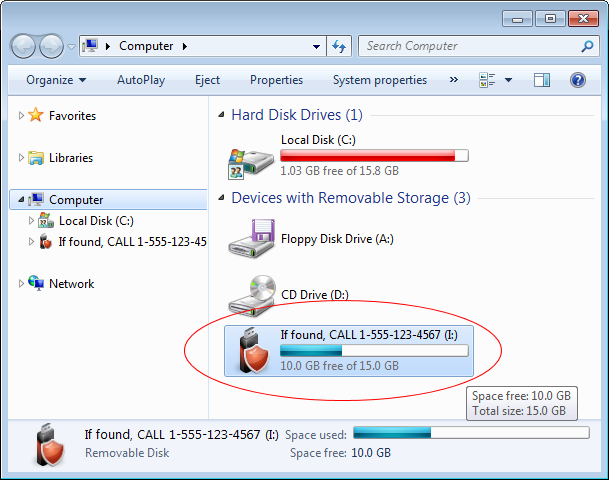
Yet another place to catch attention of the person who found the drive is the screen that appears when s/he runs the file USBCrypt.exe off the encrypted drive:
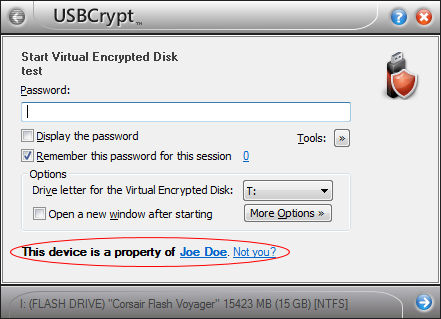
Such a message appears automatically, you don’t have to do anything special, and the name that is included in the message is the registered name that your copy of the software was licensed to (that is, presumably, your name). If the person clicks on the Not you? link, s/he will be presented with the following message:
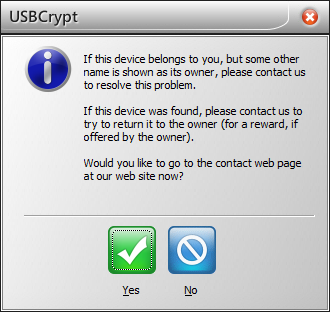
This message gives the person an opportunity to contact us with the details of the drive found, and we in turn would attempt to locate your email address in our records and let you know that someone has found your lost drive. Note that what happens after that is entirely up to you, whether you want to reward the person who found the drive or not, etc. would be entirely your decision, we would just offer you our help with getting in touch with that person.
Of course, the best solution to any such problem would be not to lose the drive in the first place. However, it’s a good idea to be prepared for such a misfortune before it might happen.