If you've used USBCrypt to encrypt your drives, you have probably wondered, how difficult would it be for someone to discover the correct password by just trying all possible character combinations until one of them unlocks the encrypted drive?
It's easy to find an answer to such a question, using the built-in Recover Password command of USBCrypt software. It's easy to find it: just try starting an encrypted drive, as usual, but instead of entering the password, click on the Tools button and select the Recover Password item on the menu:
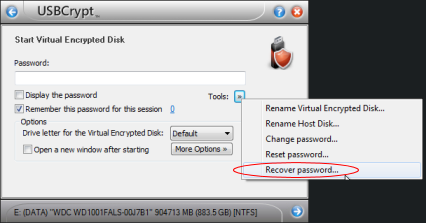
If you select the Recover Password command from the menu, the next screen will ask you to choose the character set to use for trying the passwords:
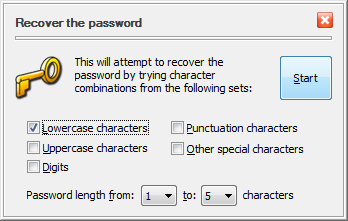
You can select the minimum and maximum length of the passwords to try, and also choose between the lower-case or upper-case characters, digits, special characters, or any combination of them. When you press the Start button, USBCrypt starts trying the passwords from the character set you've selected, in turn, until it finds one that unlocks the encrypted drive. While it's doing that, you can see the progress in a separate window, that also shows the estimated time to complete the enumeration of all possible passwords from the character set you selected:
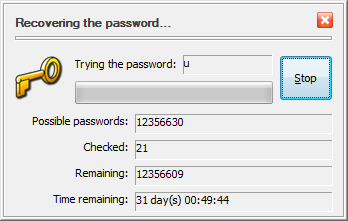
If your password is short and simple, it can be discovered rather quickly:
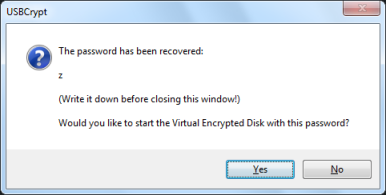
What about the more complex passwords? The time to go through them all increases rapidly with the length of the passwords and their complexity. Here are a few numbers, obtained on computer with a mid-range (as of the time of this writing) Intel i5-650 CPU:
| Characters/Maximum length | Up to 3 | Up to 5 | Up to 7 |
| Lowercase | 30 minutes | 15 days | 28 years |
| Lowercase + Uppercase | 4 hours | 1 year | 35 hundred years |
| Lowercase + Uppercase + digits | 7 hours | 3 years | 12 thousand years |
| Lowercase + Uppercase + digits + all special characters | 1 day | 26 years | 240 thousand years |
(Your numbers may be different if your computer has a different processor.)
The table above should give you a pretty good idea about the length and complexity of the password to use to keep your password safe from brute forcing. On the other hand, it can also serve as a strong reminder to take care to remember your password, because if you forget it, it may be practically impossible to recover it (unless you have created a spare key file with USBCrypt, of course.